Today, virtually every business in the world is kept on servers. Places where sensitive data is stored only on company's computers or in a paper version are almost completely gone, because the valuable information is migrated and kept in cloud systems. But this state of affairs makes the data more vulnerable to hacker attacks.
As shown in 2021 Data Breach Investigations Report by Verizon "servers are the primary targets for data breaches, consisting of a whopping 90% of security mishaps". And business owners are very much aware of that problem, investing in Cybersecurity more frequently and on a bigger scale. In the coming years, the Cybersecurity market is predicted to witness a remarkable revenue growth - by 2025, it is projected to reach an impressive figure of US$202.98bn worldwide.
Server life cycle - how can we assure your server safety?
A secured server is one that protects data and communications using various security measures, such as encryption, firewalls, and secure protocols, thereby preventing unauthorized access and ensuring safe data transmission and storage. During its lifecycle, a server goes through various stages from server build, through production to decommission. How long can one lifecycle go on for? As always, it depends on the given case.
"When it comes to the project run by NATEK Team (that includes over 100 different technologies!) the Server life cycle is planned to take its final stage by the end of each quarter. It's our duty to inform the owners of the server about the next steps in the process, and give them time for preparations and reporting any problems or concerns they might have. Open communication is crucial for the success of our operations, and allows us to bring the best results in the best time."
Piotr Kuźnar, NATEK Security Health Check Process Manager
5 stages of Server life cycle
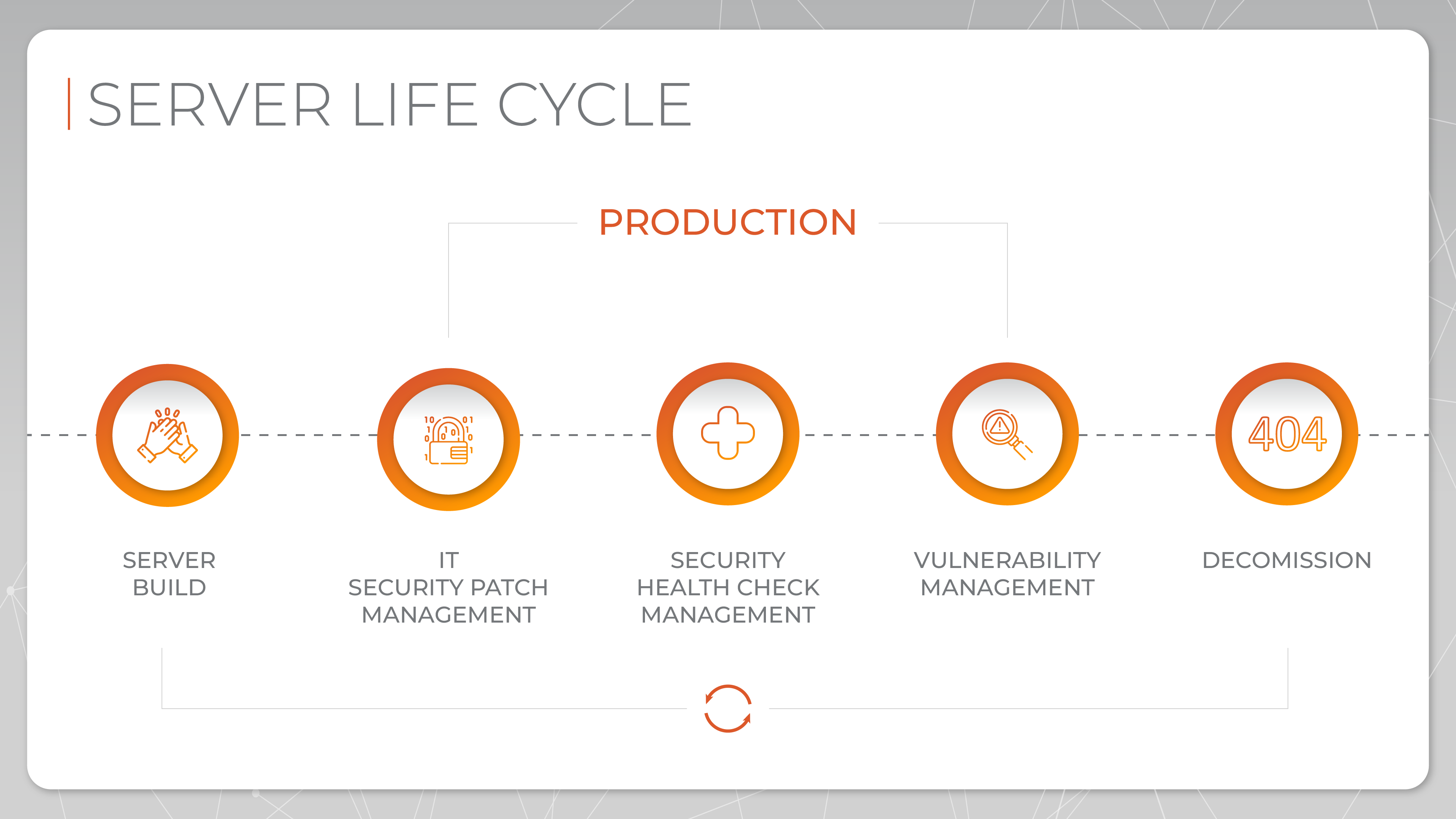
Server Build
"The goal is to build a correctly structured server right away, and implement all the necessary patches as soon as possible. It's the most important part of the Cycle, providing us with foundations for what's to come in the next steps.
As we build a server and pass it on to the Client it is configured according to the expectations of the Customer as well as the global requirements, which set a standard for businesses around the world. All that to assure maximum security for the server at all time."
Piotr Kuźnar, NATEK Security Health Check Process Manager
To build a protected server, it is necessary to predict what types of vulnerabilities might occur in the system. A Server Build Review can detect the issues listed below, which should be defused before the server launches its first activity.
- Inadequate password policies
- Exposed file shares
- Misconfigured antivirus
- Weak passwords in use
- Lack of security updates
- Default accounts in use
- Weak security policies
- Weak firewall rules
When the 1st stage of Server lifecycle is completed, it's time for the next, and most complex step - Production.
Production - IT Security Patch Management
"During the Patch Management process, our Team monitors the latest patch releases from the individual vendors month by month, quarter by quarter or year by year, and proceeds with implementing them. The more servers and the less breaks between new patches releases, the bigger is the challenge. But as long as we are organized and plan ahead, nothing can get overlooked."
Piotr Kuźnar, NATEK Security Health Check Process Manager
All patches are implemented in the structure. First preproduction, then testing and finally production. All that to avoid as many incidents as possible. Each patching is discussed and planned with the Customers, as on occasion such update might disrupt functioning of the application. But when done in advance, it will not have any negative influence on the user experience, and ultimately will bring improvement to the existing app.
Production - Security Health Check Management
The purpose of Security Health Check Management process is to verify and ensure that specific security settings are implemented according to established policies. It is intended to ensure the ongoing security and stability of the managed environment. Regular Health Checks help identify vulnerabilities, misconfigurations, and potential threats.
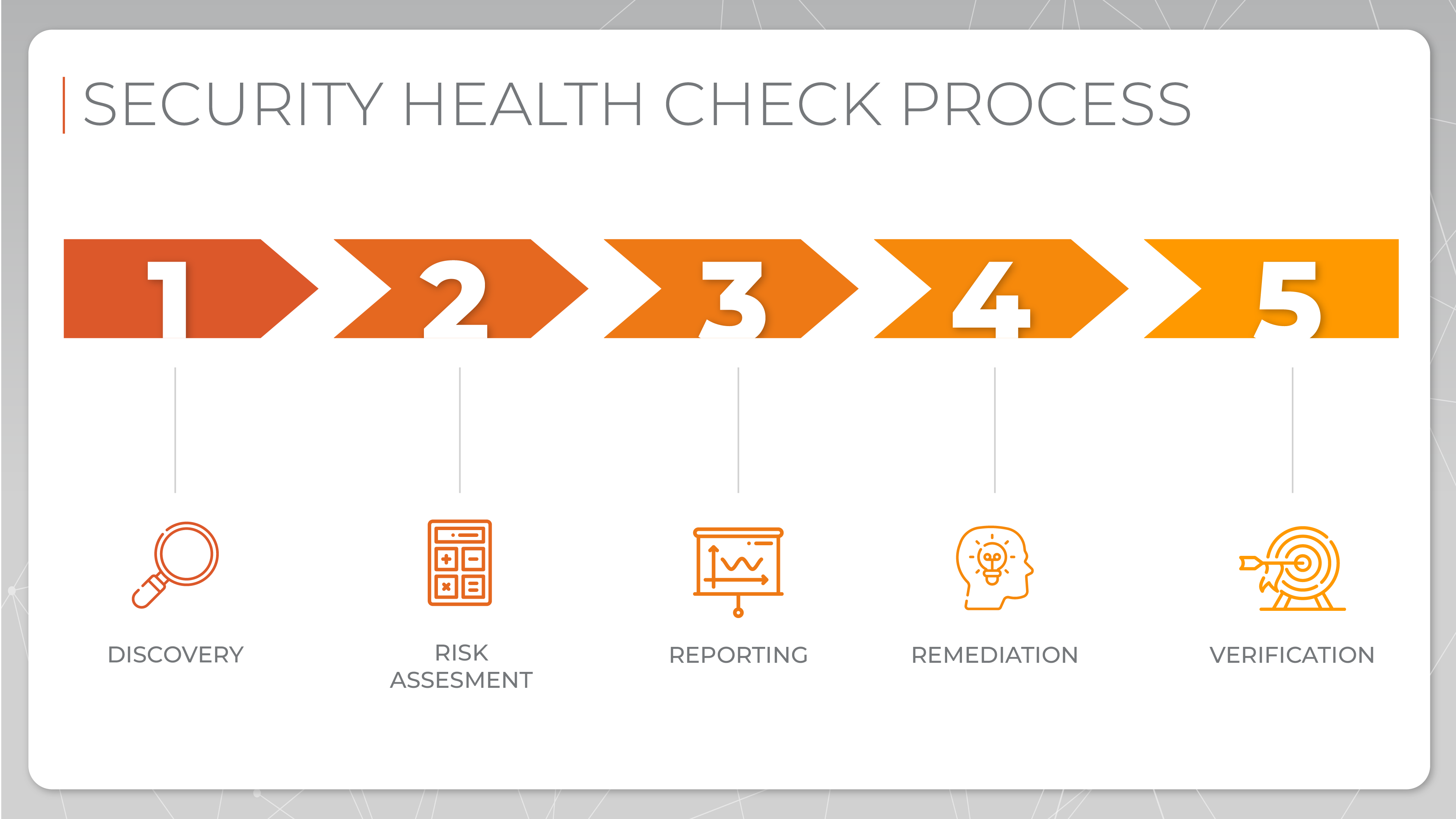
Security Health Check Process can be divided into 5 separate stages. Each of them serves a different but equally important role. Starting with Discovery, we must first create the list of servers or devices our team will be revising according to our politics. This helps us in verifying whether the implemented settings are correct, and go to the next step - Risk assessment. During cybersecurity risk assessment, we identify, analyze, and prioritize potential threats and vulnerabilities. We aim to better understand the pinpoint weaknesses of the system we are working with, and determine the possible threats, as well as solutions to avoid them.
After gathering all the necessary information, it's time for an in-depth documentation process also known as Reporting, where all the data collected during the previous stages is combined and presented in a comprehensible form. Based on this report, we can plan the following actions and continue to the Remediation phase.
"We present the Customer with issues we crossed upon, and the plan for configuration, including the proposed schedule. Then all the Server Owners are being informed, and they either give us the green light to proceed, or negotiate the start date to make sure it doesn't interfere with any important events on their side."
Piotr Kuźnar, NATEK Security Health Check Process Manager
After the patching is done, the Team Verifies and once again scans the servers under the same standards as before. Remediation is almost exclusively automated, allowing the Team to configure thousands of servers at once, and it usually takes place from 1 to 4 times a year, depending on the importance of the server. When all the deviations are gone, the process starts from the beginning.
Production - Vulnerability Management
After the Security Health Management, it's time for Vulnerability Management. It's a process of detecting, assessing, resolving, and mitigating security flaws in software and computer systems. It's an essential component of managing cybersecurity risk in IT environments. Vulnerabilities, if not addressed and patched, can expose an organization to damaging cyberattacks and data breaches.
So what's the difference between Security Health Management and Vulnerability Management? Although the processes stem from the same final goal and are based on similar steps, Security Health Management is a separate process related to servers, middleware, and network devices, where individual functionalities and actions are build by our Team based on individual Customer's needs, whereas Vulnerability Management is a commercial product/tool with built-in functionalities, licenses and specifications. What do these specifications consist of?
"The main part is always checking passwords and settings for the users. We also check all network connections, meaning all ports that are or can be open, allowing for server-to-server communication. Even though it's the users who fill in all system settings and configurations, it's our Teams job to maintain security and compliance."
Piotr Kuźnar, NATEK Security Health Check Process Manager
Decommission
Last but definitely not least, the Server's lifecycle reaches its final stage known as Decommission. When the server is no longer in use, it's extremely important to secure all the data it possesses. Depending on the case, information on the server can be migrated or deleted. Decommission often involves removing a system from service, securing its data, and disposing of its hardware and software.
Each stage of Server lifecycle has one common goal - to assure server security. But what exactly are the threats that might be lurking for your business? And how can you recognize and stop them?
Cybersecurity threats
In an ideal scenario, a Server lifecycle would run smoothly, seamlessly, with devices being added or removed under no pressure. However, in reality, every server is exposed to security threats 24/7. The Team responsible for its safety is primarily responsible for anticipating potential risks and preventing situations where an attack has already occurred. This preventative approach helps to avoid significant damage and loss, both to property and information. What cybersecurity threats do businesses most often protect against?
The best way to prevent hacker attacks from being successful is to educate the employees on recognizing, reporting and stopping the suspicious activity. With such techniques as malware, ransomware or DDoS, it's crucial that your team knows how to protect themselves and who should be the first person they inform about the incident. That's why frequent change of passwords and verification of users with access to various information is so important, and the absolute baseline for all other much more complicated procedures. In case of Insider threats, it's the people "on the inside" that might make the most damage. So to keep your business safe, always remember that the principle of limited trust is useful not only in road safety, but also cyber safety.
"Our cyberattack response is primarily preventative. Our mission is to prevent any data or other corporate assets from falling into the wrong hands. Thanks to our thoroughness and diligence, we can boast about a record of zero DDoS attacks. That said, our Team is always on duty, ready to handle even the most complicated scenarios."
Piotr Kuźnar, NATEK Security Health Check Process Manager
Is Server Security a necessity for a modern business?
"The answer is simple - yes. All servers connect to the internet, and as a result, they become accessible not only to business owners, employees or potential customers, but also to unauthorized persons. Therefore, maintaining the highest possible level of security should be a priority for every company, especially those whose security also affects the security of their customers or users, e.g. banks. All bugs and system holes must be checked and repaired/removed on an ongoing basis, and this requires the employment of a dedicated team whose full attention will be devoted to this issue."
Piotr Kuźnar, NATEK Security Health Check Process Manager
If you are looking for a professional Team of Experts with years of experience in providing services in the field of cybersecurity and server security, do not hesitate to contact our NATEK Sales Prospection Team Lead Andrzej Osman at andrzej.osman@natek.eu or go fill out our Contact form to begin our cooperation and #growITwithus!