Modern businesses of all sizes rely on cloud services to store data, run applications, and deliver services online. But how many of them utilize this tool in a correct and, more importantly, safe way? Recklessness isn't a new concept, even (or maybe especially) in the case of big enterprises, which on the surface showcase various security policies but in practice often put convenience and financial savings above efficient and preventative solutions.
Security breaches are a real threat, and if not prepared, it's not a question of IF they will happen but WHEN. So how can companies ensure the safety of their data? The answer isn't as complicated as one may think. Together let's clarify the basic rules of safe cloud use, understand the Shared Responsibility Model, explore Secure Cloud Foundation in Microsoft Azure, and find out what mistakes to avoid based on real-life cases.
Secure Cloud Foundation in Microsoft Azure
All established cloud providers, such as Microsoft Azure, Google, and AWS, have a well-architected framework based on 4 main security pillars:
- Identity & Access
- Network Security
- Data Protection
- Logging & Monitoring
Obeying those guidelines is usually enough to keep your cloud and all the data it stores protected. To make it even easier for the users, Microsoft Azure is equipped with convenient-to-navigate Azure Verified Models that you can modify to your needs and create the Landing Zone and Application Landing Zone for your project. What are they?
Picture Landing Zone like a neighbourhood blueprint: it defines where things go, how traffic flows, and what the rules are. Before you build your house (your app), the street, lighting, and fences are already in place. It includes, among other things, networks, policies, and access distribution, and it is a foundational cloud environment for an entire organization intended for platform and cloud foundation teams.
Next in line is the Application Landing Zone - a workload-specific environment built on top of the Azure Landing Zone meant for application and product teams. Its main purpose is to provide everything an application needs to run securely and consistently, including (but not limited to) app-specific subscriptions or resource groups, application networking, compute, storage, databases, app-level security, monitoring, CI/CD, scaling, and availability settings. It's like a building constructed within the city.
Following security benchmarks is essential
Utilizing the available tools to create a safe foundation for your cloud is not a suggestion but an obligation. As a business using the cloud, you are to follow a set of universal security benchmarks that clearly state how to be compliant with the latest rules. Microsoft Cloud brings together all those various guidelines, like CIS (Critical Security Controls), PCI (Payment Card Industry), and NIST (National Institute of Standards and Technology) Controls, and delivers you a ready solution.
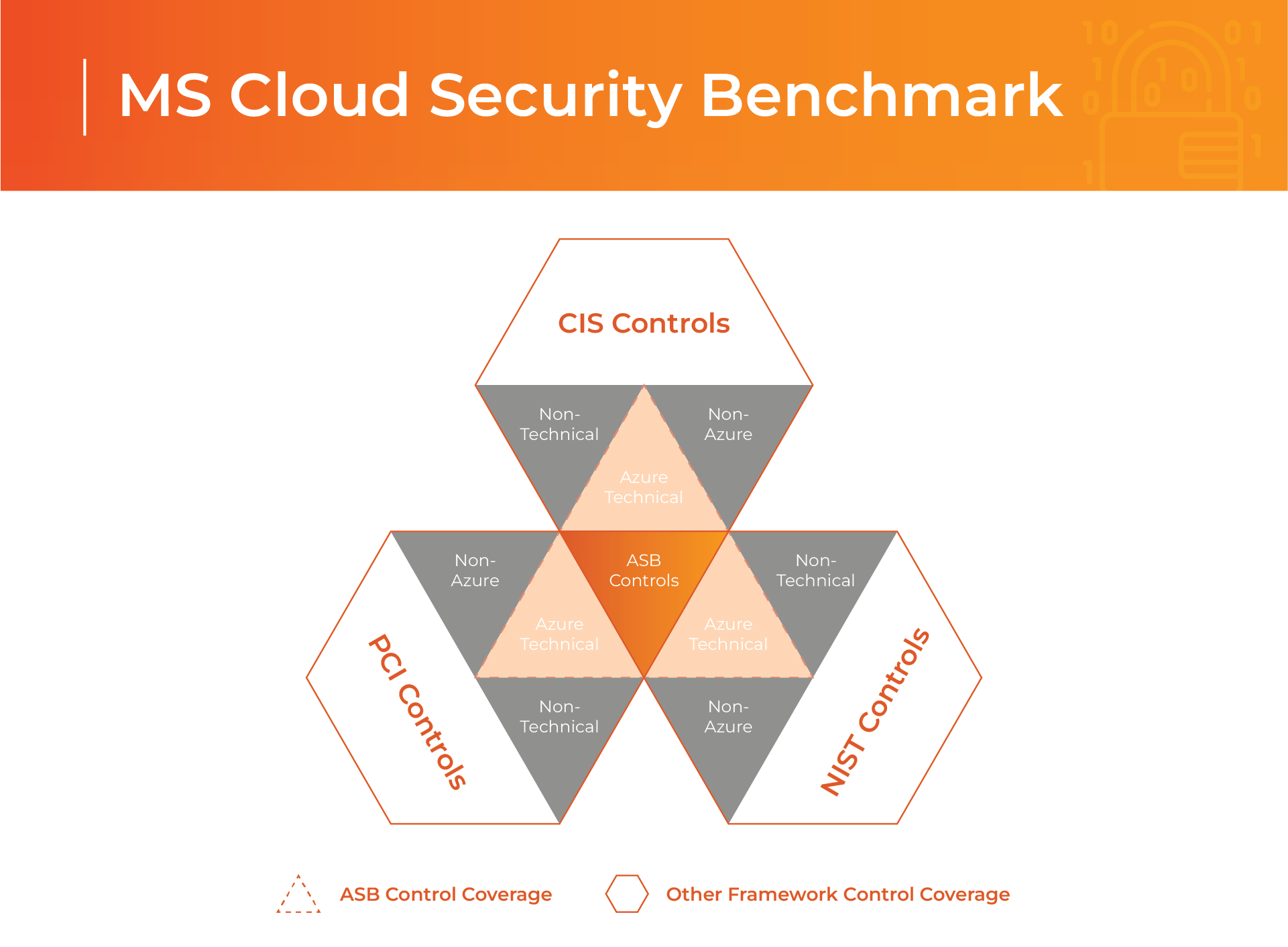
Thanks to the mentioned functionalities, the security team experts can design security policies and baselines customized to your organizational needs and review the policies implementation and enforcement to stay compliant with the applicable benchmarks. All that can be vastly improved with automation, which allows for repetitiveness. Being able to deploy your infrastructure as code directly to the cloud facilitates the security procedures and allows the team to focus on more complicated tasks that ensue.
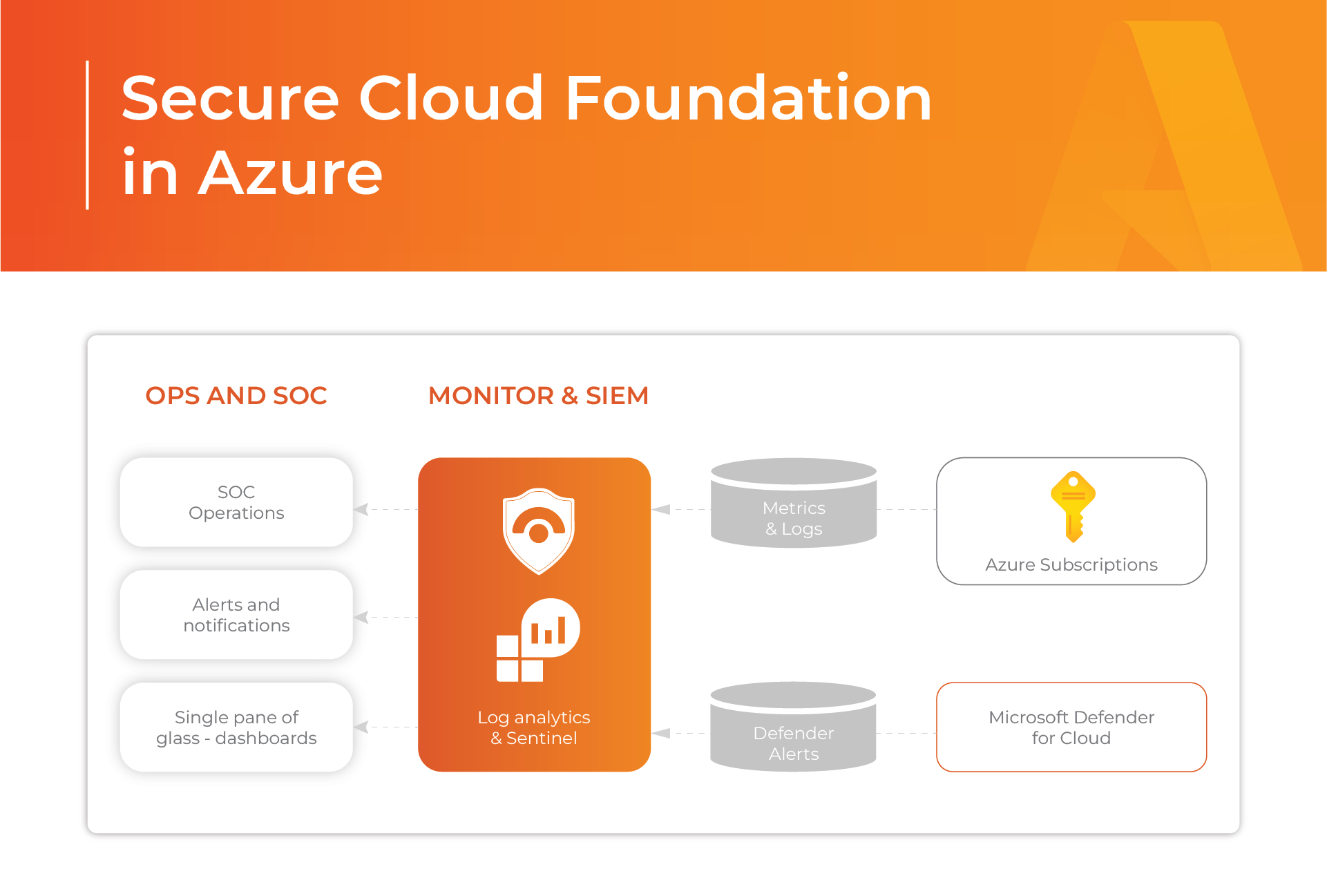
Cloud Monitoring Procedures
When your foundation is prepared in the correct way and your application has been deployed, you can follow up on all the security requirements by monitoring the occurring incidents. Once again, Azure comes prepared. Thanks to Microsoft Defender for Cloud and metrics and logs coming from Azure subscriptions, the security team stays aware and alert to any potential anomalies, including those that may result in a breach.
Last but not least, Azure allows you to build your very own AI RAG based on your company's data, creating a unique context for the results creation. Microsoft is spending tens of billions per year on AI-related cloud infrastructure improvements for Azure. These investments are focused on compute power, data centers, chips, and networking that enable Azure to host and scale AI services like Azure OpenAI, Copilot, and other generative AI features. But remember the rules of safety. The tool you create must be deployed in a private mode, which is enforced by Azure policies and Defender for AI Services policies. Limit the access controls and always pay attention to suspicious activities to keep your AI engine protected.
What is the Shared Responsibility Model about?
Let's start with the most important part - basic rules of being a responsible cloud user and an accountable cloud service provider. For the data center to be fully protected, the two mentioned entities must cooperate like a well-oiled machine. The aptly named Shared Responsibility Model (visible below) in cloud computing defines which security and operational tasks are handled by the cloud provider and which are the responsibility of the customer. The simplest principles are:
▪ Cloud CUSTOMER is responsible for the security IN the cloud
▪ Cloud PROVIDER is responsible for the security OF the cloud
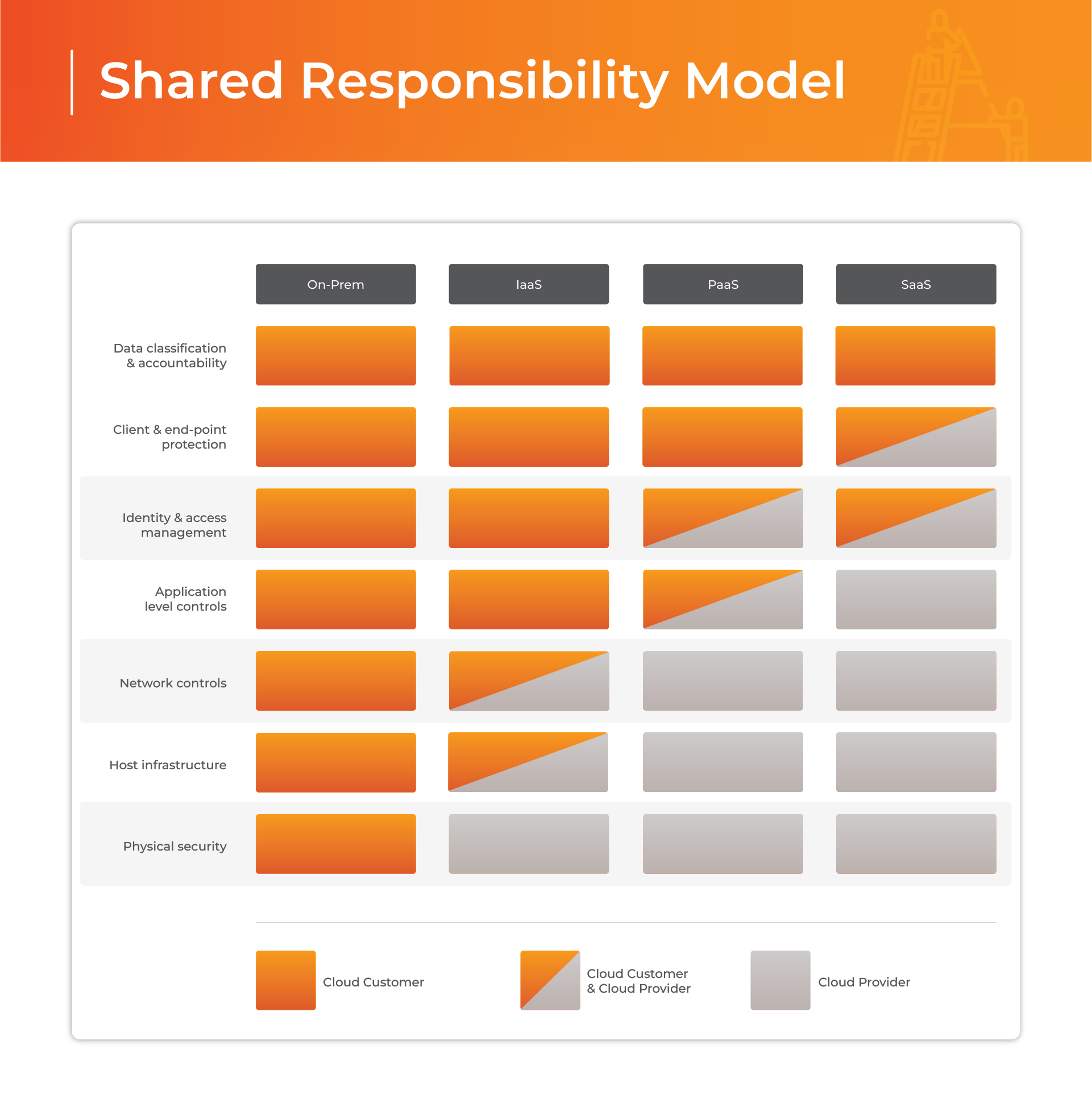
Customer security responsibilities cover what they put on the cloud: data, applications, access management, and configuration. This means customers must handle tasks like setting strong passwords, managing user permissions, encrypting sensitive data, and properly configuring cloud services. On the other hand, cloud provider responsibilities usually include securing the physical infrastructure, networks, servers, and core services. For example, AWS, Azure, or Google Cloud ensure their data centers are protected, patched, and compliant with regulations.
With years of experience in IT outsourcing, NATEK Team understands the challenges that may appear during long-term cooperations. We base our strategy on 3 core Values: Partnership, Expertise and Accountability, which makes us the perfect mediator and support for both sides of a collaboration. What can we contribute to the process?
- Guiding configuration and compliance: Ensuring the customer sets up cloud services correctly and follows security best practices.
- Monitoring and management: Continuously tracking performance, security, and usage so the customer meets their responsibilities while leveraging the provider’s infrastructure effectively.
- Bridging expertise gaps: Translating technical cloud capabilities into practical solutions for the customer and handling communication or escalation with the cloud provider when needed.
As NATEK, we can ensure both parties fulfil their roles under the shared responsibility model, reduce risk, and maximize the benefits of cloud adoption. And in the world of quickly evolving and upgrading tools and technology, such expertise might turn essential.
Data security breaches and disaster recovery examples
One of the most common mistakes made while using the cloud is filling it with data with no rhyme or reason behind it, which results in the number 1 security issue in the cloud - Misconfiguration of complex cloud features. Why? Because users commonly tend to work with the default settings, that may include publicly open key vaults (lack of RBAC (Role-Based Access Control), private endpoints), Kubernetes clusters not in private mode, NSG (Network Security Group) open to the internet, and no MFA (Multi-Factor Authentication). The unfortunate results of such negligence are often reflected in the additional costs that are necessary for disaster recovery procedures. Let's take a look at some of the most widely known cases of what happens when you don't follow the motto "better safe than sorry".
NATEK Case Study for Cloud Safety
After joining a FinOps project for a big billion-euro company, our Team quickly discovered various security vulnerabilities in their cloud, including exposing critical and confidential databases to the public Internet. Not only were those a threat to an extensive amount of data, but the business was also facing potential penalties due to not being compliant with GDPR regulations. In the worst-case scenario, such oversights could have resulted in up to millions of euros in fines.
Our Team took care of the issues starting from the basics – rebuilding the infrastructure and applying all the security protocols and procedures enforced by Microsoft. Thanks to the efficient identification of the problem and the immediate implementation of security procedures in line with the latest guidelines, the company avoided both huge financial penalties and a damaging blow to their reputation on the market.
Samsung Smart TV (2014)
A fire at one of Samsung’s data centers caused major outages for Smart TVs, disabling apps, streaming services, and online features for many users. Although the TVs themselves were undamaged, their reliance on cloud-based servers made them partially unusable when the servers went offline.
The incident highlighted the risks of centralized infrastructure and how cloud outages can directly impact everyday consumer devices. In response, Samsung moved its Smart TV services to a more distributed cloud architecture, improving redundancy, reliability, and recovery times. This shift made its services more resilient, scalable, and less vulnerable to localized failures.
SNOWFLAKE (2024)
In 2024, Snowflake suffered a major data breach after attackers exploited accounts without enforced multi-factor authentication (MFA), allowing them to access and exfiltrate sensitive customer data. Several organizations were affected, including financial institutions, which faced heightened regulatory and confidentiality risks.
The incident highlighted the critical importance of strong identity and access controls in cloud environments. Snowflake responded by enforcing MFA across all accounts, revoking compromised credentials, and strengthening monitoring and security practices, reinforcing the need for proactive security measures to prevent similar breaches in the future.
Cloudflare (2025)
In November 2025, Cloudflare, a leading cloud and web security provider, suffered a major outage that made dozens of popular websites and apps (including social media, AI tools, and ride-hailing services) unreachable for several hours. The disruption was caused by a configuration error in Cloudflare’s internal systems, not a cyberattack, and no customer data was compromised.
The incident underscored how reliant millions of businesses are on a few cloud providers, as even functioning company servers couldn’t serve users without Cloudflare’s routing. Following the outage, Cloudflare improved redundancy and safeguards, highlighting the importance of diversified cloud architectures and contingency planning.
NATEK can help you in managing cloud services
Investing in prevention rather than waiting to fix problems is always the smarter approach, especially in cloud and IT environments where outages, breaches, or misconfigurations can have far-reaching consequences. Proactive measures, such as enforcing multi-factor authentication, implementing robust monitoring, designing redundant architectures, and conducting regular security audits, help avoid costly downtime, reputational damage, and regulatory penalties. While prevention requires upfront effort and resources, it drastically reduces the likelihood of crises, ensures business continuity, and builds trust with customers, making it far more effective and economical than reacting to incidents after they occur.
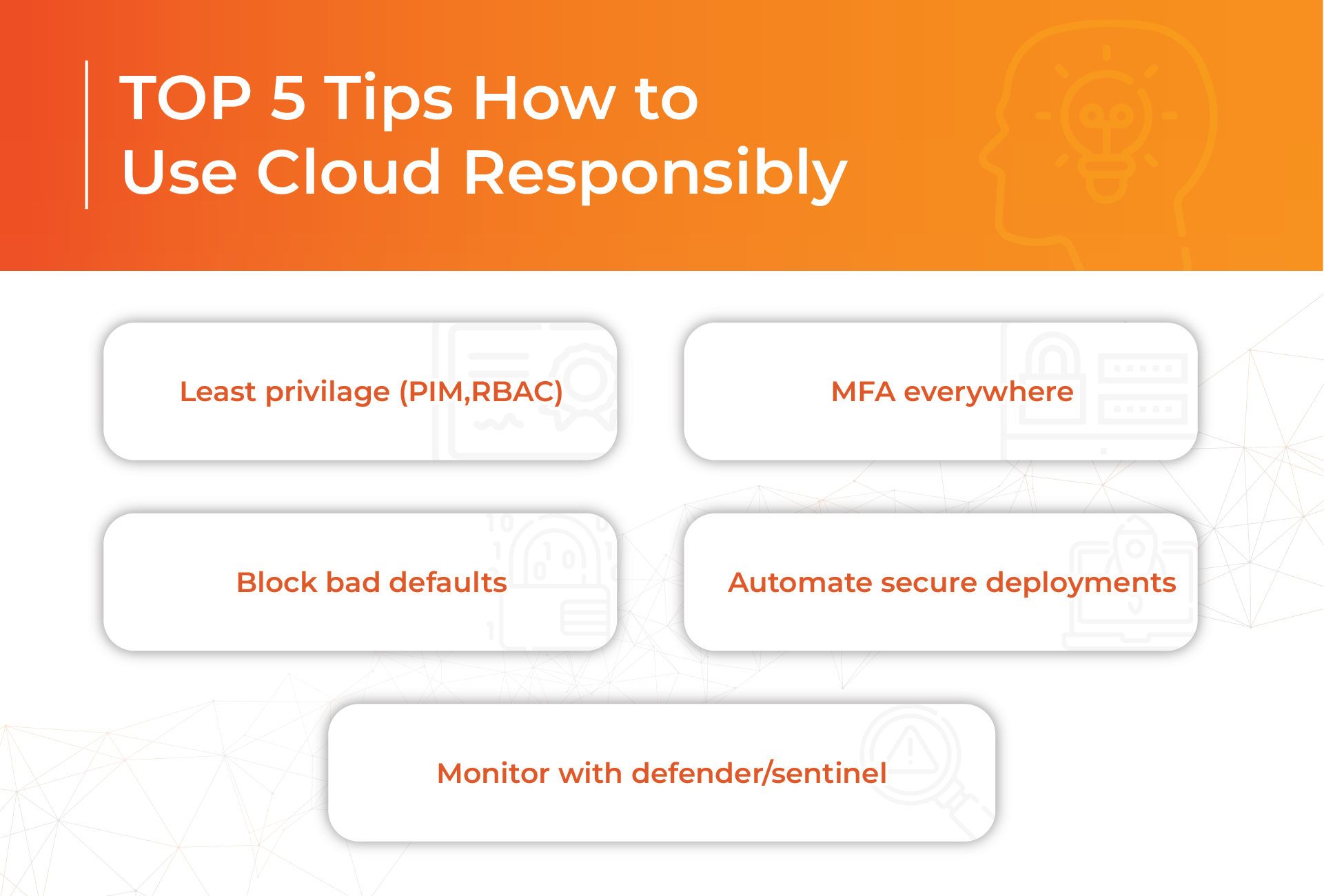
We summed up the most crucial TOP 5 rules of cloud safety in the graphic below. Save it for later to save your data from getting into the wrong hands.
If you are looking for a reliable Team of Cloud Experts with years of hands-on experience delivering cloud transformation, management, and cost-optimization solutions for Fortune Global 500 companies worldwide, do not hesitate to contact our NATEK Sales Prospection Team Lead, Andrzej Osman, at andrzej.osman@natek.eu, or fill out our Contact Form to start our collaboration. #growITwithus and build secure, scalable, and efficient cloud solutions that drive lasting success.